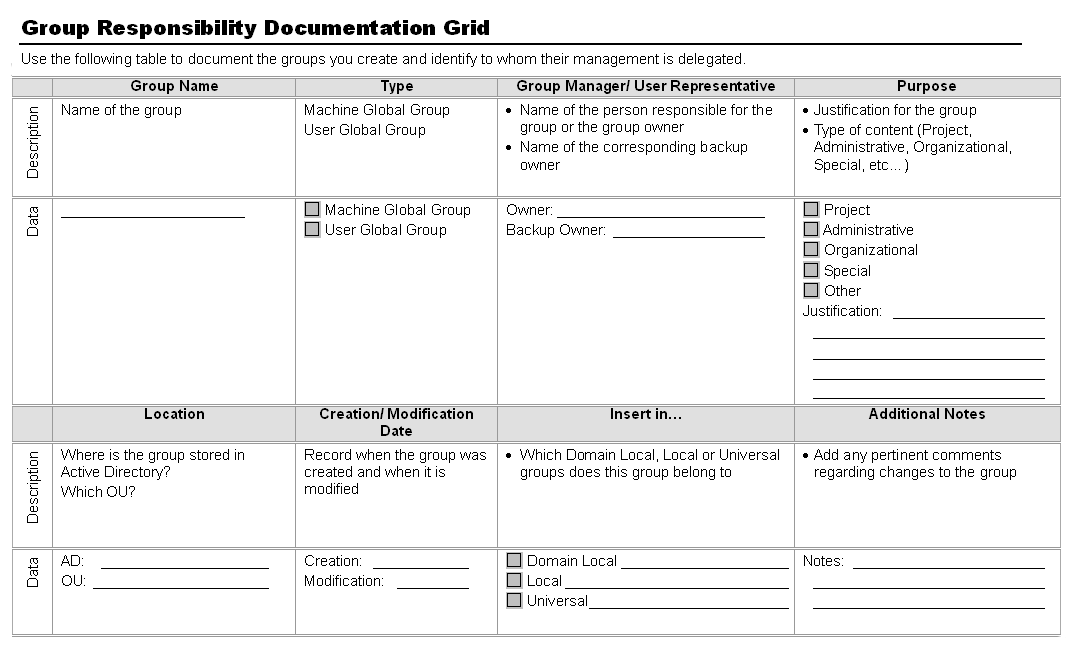
Table 1. Document Your Groups
Make sure to outline your groups outside your directory using external databases. This lets you keep a tight leash on changes that occur in your organization to snuff out possible security leaks.
|
| ||

|
|
|
Table 1. Document Your Groups Make sure to outline your groups outside your directory using external databases. This lets you keep a tight leash on changes that occur in your organization to snuff out possible security leaks. | |